Cybersecurity
Security is not a product, it’s a process to protect your business
secure the digital enterprise against cyber attacks
IT has changed the way we work today. Enterprises and individuals rely on IT more than ever before and companies deploy the latest modern communication infrastructures such as clouds, smartphones, wireless, collaboration solutions as well as intelligent data center and storage solutions. As we move to be more data dependent and customer experience being the core of digital transformation, we need to protect the digital enterprise against cyber attacks and accelerate transformation with care.
As many organizations have learned, it’s no longer a matter of if you’ll face a cyberattack, it’s a matter of when you will be struck. Every asset in your organization is at risk. Attackers can hack indiscriminately or target specific assets, preying on regardless of the size of the organizations in the public and private sectors. Exposing the attackers requires defenses that identify each threat, even when it adopts the colors of its target environment.
We can help you protect your business by building a cybersecurity foundation, detecting cyber threats you are facing and responding to a cybersecurity breach. Together, we can help you deliver better outcomes and long-lasting results, from strategy to execution.
Advise
At Emitac we proactively monitor cyberattacks by leveraging machine learning techniques to analyze and correlate the data and advising on your security strategy depending on your current level of security maturity.
Some of the services include:

INVESTIGATING
UNDERSTANDING
SOLVING
PROTECTING

24/7 MONITORING
Protect
PROTECT
Protect the IT environment based on End-to-end visualization of Hybrid assets and network topology
Real time
Real-time triage and solution for any misconfigurations
ASSESS
Assessments of network ports on a time-limited basis according to the requirements, ensuring a closed-by-default based in SOPs
DETECT
Detecting security risks and threats through quick analysis of the network attack surface
SECURE
Security assessment and risk tolerance to evaluate our enterprise security needs and develop a strong roadmap and architecture that supports the digital ambitions
STREAMLINE
Access management through robust processes and technologies that streamline access to the IT Environments
defense
Cloud data protection and active defense mechanism
PROTECT
Protect the IT environment based on End-to-end visualization of Hybrid assets and network topology
Real-time
Real-time triage and solution for any misconfigurations
assess
Assessments of network ports on a time-limited basis according to the requirements, ensuring a closed-by-default based in SOPs
detect
Detecting security risks and threats through quick analysis of the network attack surface
secure
Security assessment and risk tolerance to evaluate our enterprise security needs and develop a strong roadmap and architecture that supports the digital ambitions
streamiline
Access management through robust processes and technologies that streamline access to the IT Environments
defense
Cloud data protection and active defense mechanism
Monitor
24/7 security monitoring and IR to detect threats, including system policy changes and compliance violations
Consistent base data across business units
Consolidation of forecast & target data across groups, helping to respond to the market faster
Building data infrastructures, solving data quality problems & manage master data
Improved planning & reporting quality from data cleansing
Real-time measurement of business performance
24/7 security monitoring and IR to detect threats, including system policy changes and compliance violations
Consistent base data across business units
Consolidation of forecast & target data across groups, helping to respond to the market faster
Building data infrastructures, solving data quality problems & manage master data
Improved planning & reporting quality from data cleansing
Real-time measurement of business performance
Our Penetrating Testing Services
Security and compliance are business dilemmas that most face regularly.
Emitac offers to test your website by manually simulating an attack from a hacker to see if there are security holes that could compromise your sensitive data. We learn your vulnerabilities and the ways in which attackers could exploit them.
With that in mind, Penetration Testing Services team will simulate a real-world attack on your networks, applications, devices, and / or people to demonstrate the security level of your key systems and infrastructure and show you what it will take to strengthen it.
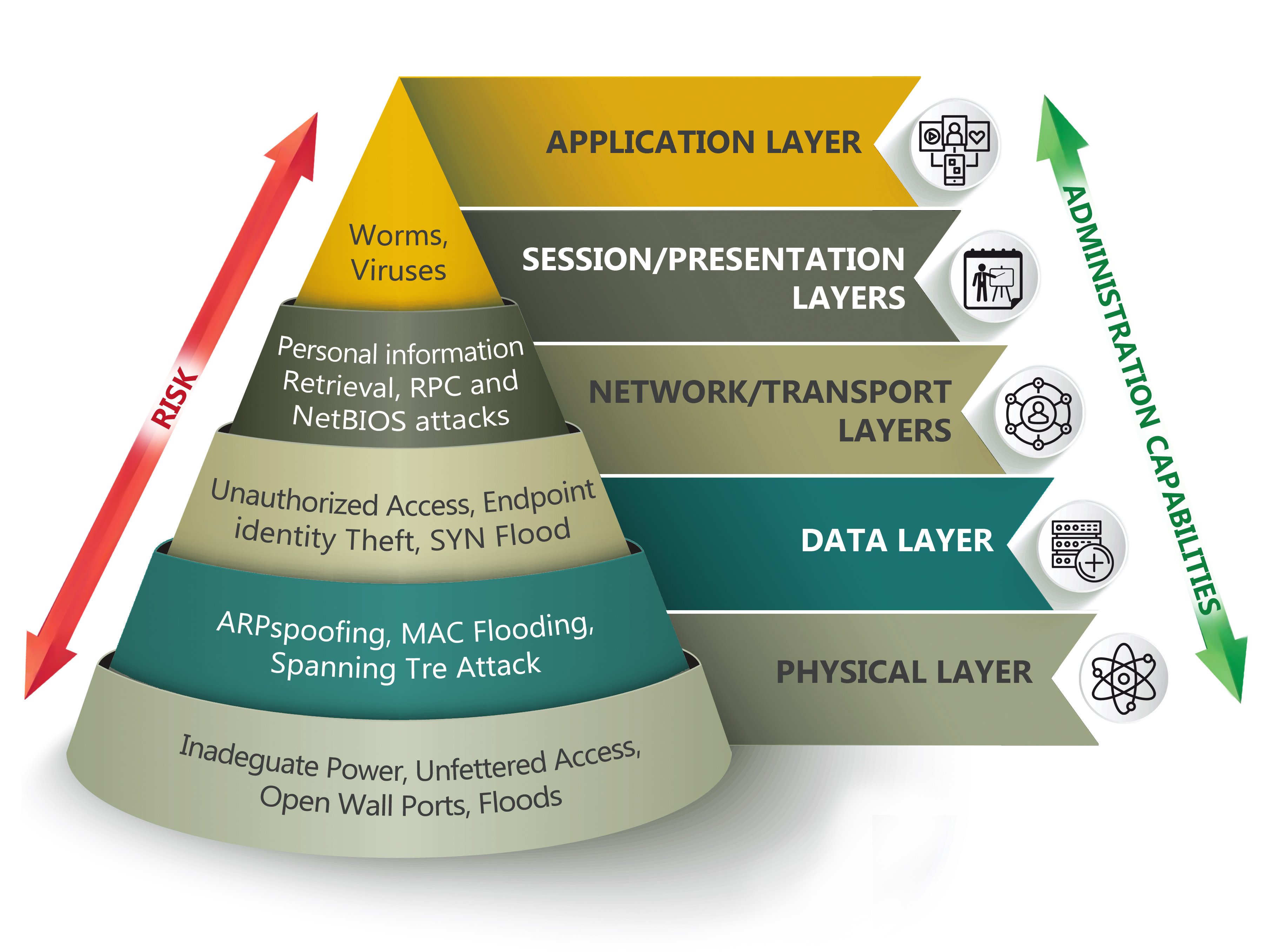

Network
Web Application

Mobile Application
Social Engineering

Wireless Network
Vulnerability Assessment
The data is every way and accessed by a lot of open source software. They don’t maintain the latest software revisions, have unnecessary services and port exposed to the Internet but are unaware of the security holes they are introducing.
We offer different types of vulnerability assessments to address all the security aspects





